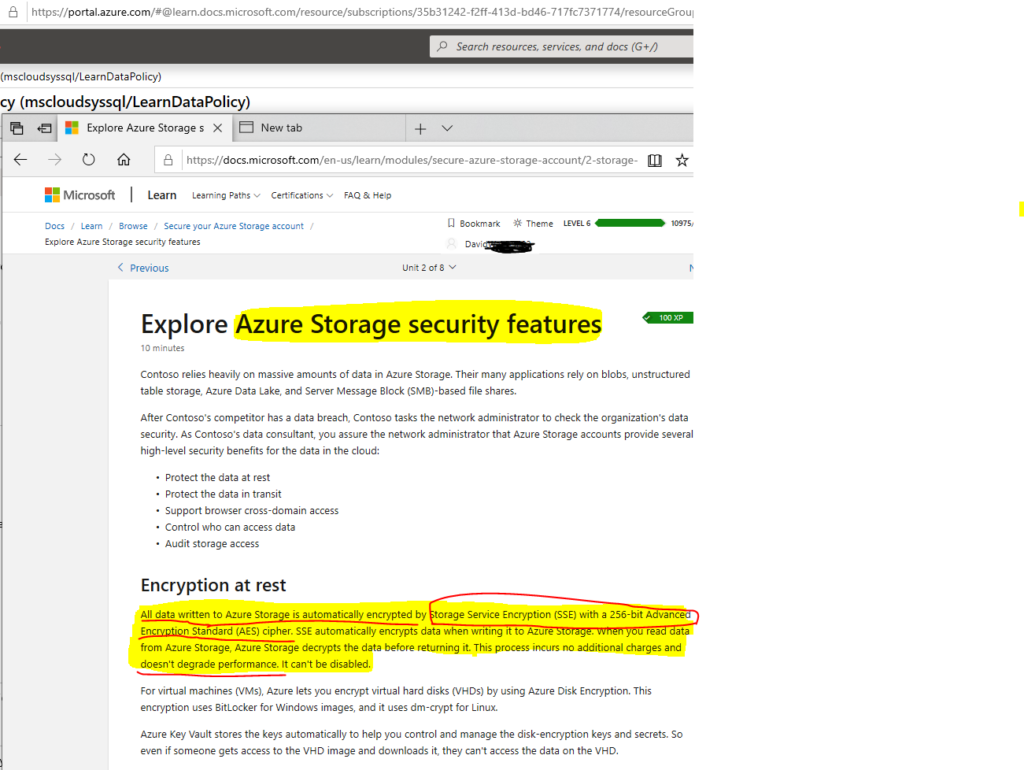
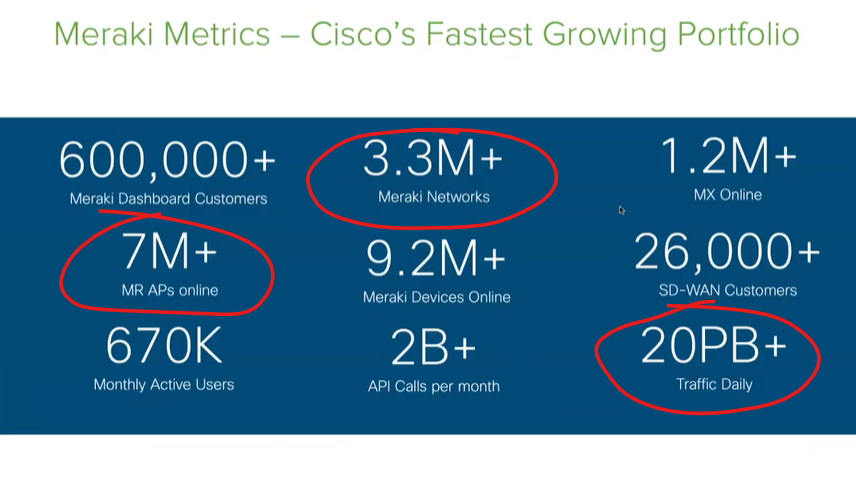
This is a useful webinar or video of Cisco Meraki administration (link below). Meraki is the ultimate cloud-managed solution, in my opinion. I use it at my job and can verify that it is a solid product, possibly one of the best out there in the networking world. It is ubiquitous and seems to be growing even more steadily, as evidenced below. These are very impressive statistics, especially the 20 PB (petabytes) of daily traffic – we do not see PB referenced a lot even in the modern data-driven world. But 20 PB DAILY is a LOT of data!
The webinar gets very good once you pass the first 5 introductory minutes. It is geared towards Meraki in schools, but the basics of how Meraki simplifies network management complexity are covered. Besides, universities, public or private K-12 schools, along with all businesses and entities all need to have reliable, safe, and secure networking and proper management tools.
Some items covered are Meraki WiFi, and IoT and switch device management. Also covered are rules for a Meraki network – example given was a simple block of bit torrents, which are files that are truly detrimental to any and all networks. Finally, the Cisco webinar covered environmental sensors and video cameras. Meraki is very advanced with these last two areas. Network administrators can monitor video cameras and sensors in real-time because they too are networked via IP and connected within the Meraki environment. The video management is highly detailed and advanced. There is no need for additional storage nor is there a need for video software to watch the videos, given that the videos are viewed within the Meraki interface (they can be shared or exported from there if needed). And sensors such as temperature controls can be remotely configured and monitored as well.
This is the link to the Meraki webinar: